Embedded Hardware
Dive Into The World of Embedded Hardware Forensics! The Teel Technologies 5-day Embedded Hardware Acquisition & Analysis Forensic Training will focus on processes that examiners can use to access digital data at the logical and physical levels from sources that include: IoT, Smart TV's, Vehicle Systems, Skimmers/Shimmers, and almost every other device that utilizes a main board, controller chip and some forms of flash memory.
Description
*Please Note: All prices listed are in USD
Students will be provided with a foundation of how electronics work in relation to the techniques being used in this training. The processes taught will include tools from cost effective sources, open source resources, and commercial tools.
Students will learn how to adapt techniques like JTAG, ISP, Chip-Off, and apply it to embedded communication protocols such as SPI, i2C, UART and more, in order to exploit components and recover data from various sources like embedded code and the flash memory of controller chips. Data from these sources can then be analyzed for evidence or malware artifacts.
Prerequisites
This course is open to all digital forensic professionals.
Due to the sensitive nature of our curriculum, and industry, all potential students are subject to vetting prior to enrollment. We reserve the right to refuse registration to any person that does not meet our established criteria.
Course Itinerary
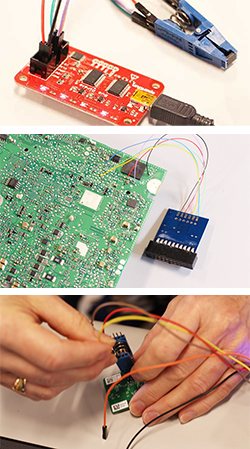
Day 1 Overview
- Introduction to IoT
- Digital Communications
- Smale Scale Computers
- Logic Analyzers
Day 2 Overview
- Electronics
- In System Programming Connections
- Multimeter
- Bluetooth
Day 3 Overview
- JTAG Signal Lines
- Skimmers / Shimmers
- Serial Peripheral Interface (SPI)
- Hacking Hardware - Bus Pirate
- Research
Day 4 Overview
- i2C Communications
- ASIX Programmer
Day 5 Overview
- Applying hands-on knowledge to acquire and analyze various IoT devices
Evaluation Procedures:
All students receive a certificate of completion.
Included with Training

Included with Training:
Embedded Hardware Forensics Toolkit
Due to frequent updates and changes in equipment, actual training and class giveaways may change.
Laptop Requirements
- Windows PC with two (2) USB A ports.
- Windows OS
- macOS with Bootcamp Windows
- macOS alone will not work (No Virtual Machines)
- 8GB RAM (minimum)
- 100GB storage (minimum)
- You must have admin rights or have the admin password for software installation.
- NOTE: ALL Windows updates should be done prior to class.